Multi-hop sessions
This feature requires HCP Boundary or Boundary Enterprise
Most organizations want to provide access to infrastructure without exposing private networks. Many organizations also have complex network topologies requiring inbound traffic to route through multiple network enclaves to reach the target system. Multi-hop sessions allow you to chain together two or more workers across multiple networks to form reverse proxy connections between the user and the target, even in complex networks with strict outbound-only policies.
Multi-hop sessions let you connect to private endpoints without necessarily opening inbound access to isolated or private networks. By allowing outbound access from an egress worker in the private network to an upstream worker on a specific port, a Boundary client can access the target using a secure tunnel that is initiated by an ingress worker in the chain.
Introduction
Multi-hop sessions introduces five concepts for how workers function. You can categorize them from the point of view of a client and a worker.
From a worker perspective, the following concepts apply:
- Upstream worker: A worker that is closer in hop count to a controller. Upstream workers receive join requests from downstream workers.
- Downstream worker: A worker that is closer in hop count to a target. Downstream workers initiate connections to upstream workers.
From a client perspective, the following concepts apply:
- Ingress worker: A worker that Boundary clients connect to. It is the first worker in the multi-hop chain.
- Intermediate worker: A worker with upstream and downstream workers in the chain. These workers provide the fabric for multi-hop from ingress worker to egress worker.
- Egress worker: The last worker int he multi-hop chain. Boundary client connections egress the proxy chain at this worker to reach the target.
Note that ingress, intermediary, and egress are general ways to describe how the respective worker interfaces with resources. A worker can act as more than one of those at a time.
Multi-hop worker capabilities
Multi-hop capabilities, including multi-hop sessions and Vault private access, is when a session or Vault credential request goes through more than one worker. To enable this, you must connect two or more workers to each other in some configuration. There are no limits on the number of workers allowed in a multi-hop session configuration.
In the diagram below, Worker 1 is considered an upstream worker to Worker 2. Worker 3 is a downstream worker to Worker 2. As such, Worker 2 is an intermediate worker in the multi-hop chain. If there was a target behind Worker 3, and end users connected to Worker 1, then Worker 1 is the ingress worker and worker 3 is the egress worker.
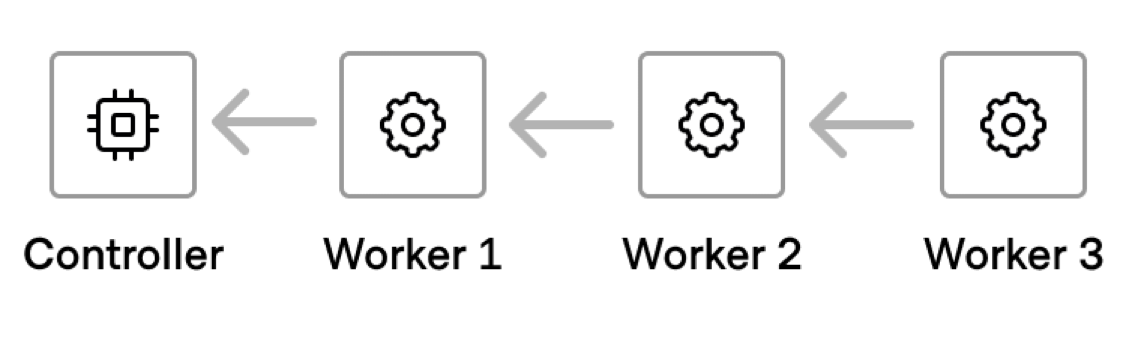
You can deploy multi-hop workers in scenarios where inbound network traffic is not allowed. A worker in a private network can send outbound communication to its upstream worker, and create a reverse proxy to establish a session.
Multi-hop worker requirements
To configure multi-hop sessions, you must deploy Boundary self-managed workers into various networks. When you deploy multi-hop workers, it is important to configure worker tags that establish ingress and egress workers.
From a networking perspective, multi-hop workers have the following requirements:
- Downstream worker: Requires outbound access to the proxy listener on the upstream worker (default 9202).
- Upstream worker: Requires inbound access on the proxy listener port from the downstream worker IP or network.
An intermediary worker can function as an upstream and downstream worker simultaneously. Intermediary workers require outbound access to the proxy listener on the next upstream in the chain. They also require inbound access on the proxy listener port from the downstream worker IP or network that connects to the intermediary worker.
Intermediary workers are optional. A multi-hop chain can consist of only two workers, an ingress worker and an egress worker. If you want to use more than two workers to reach a target, you must configure network requirements for intermediary workers.
The downstream worker that is closest to the target is an egress worker. The egress worker requires outbound access to the target IP and port.
The upstream worker that is closest to the client is an ingress worker. The ingress worker requires outbound access to each controller cluster listener port (default 9201) as well as inbound access from Boundary clients on the proxy listener port (default 9202).
Target worker filters
You must configure target worker filters for workers to allow for fine-grained control over which workers handle ingress and egress for session traffic to a target. Ingress worker filters determine which workers are used to intiate a session. Egress worker filters determine which workers are used to access targets at the end of the multi-hop chain.
Complete worker configuration
For the full set of worker parameters and a complete configuration example, refer to the worker stanza documentation.